Reviewed and Approved by Tim Lombardo, Senior Director, Food Consulting Services, EAS Consulting Group, a Certified Group company.
1-Minute Summary
- Food defense is the protection of the food supply from intentional contamination.
- FDA 21 CFR 121 (Mitigation Strategies to Protect Food Against Intentional Adulteration) mandates that food manufacturers develop a food defense plan.
- Requirements include a vulnerability assessment and actionable process steps (APS), if needed. And then, if one or more APS are identified, there are further requirements for mitigation strategies, monitoring, corrective actions, and verification.
- Several tools exist to help perform a vulnerability assessment to identify gaps in your processes.
- Ongoing monitoring and revision of your food defense system is required to stay current with emerging threats.
Understanding and Implementing Your Food Defense Plan
While most food safety and quality assurance professionals understand the importance of food defense, creating a robust food defense plan is where many challenges arise.
To meet regulatory expectations, particularly those outlined in 21 CFR 121 of the Food Safety Modernization Act (FSMA) – the “Mitigation Strategies to Protect Against Intentional Adulteration,” or IA, rule – a well-defined food defense strategy is vital.
This article explores what food defense encompasses, why it’s necessary, and how to develop an effective plan to safeguard your operations.
Compliance with Regulations and Standards
Let’s take a closer look at the regulations first.
The Intentional Adulteration Rule, mentioned above, mandates that businesses develop and maintain a food defense plan.
21 CFR 121.126 states:
- Requirement for a food defense plan. You must prepare, or have prepared, and implement a written food defense plan.
The regulations also define the content of your food defense plan, which must include…
- The written vulnerability assessment, including required explanations, to identify significant vulnerabilities and actionable process steps.
- The written mitigation strategies, including required explanations.
- The written procedures for monitoring the implementation of the mitigation strategies.
- The written procedures for food defense corrective actions.
- The written procedures for food defense verification.
Failure to meet these regulatory obligations can lead to severe consequences, including substantial fines, mandatory recalls, legal action, and damage to a company’s reputation. Non-compliance also increases the risk of unaddressed vulnerabilities, potentially leading to intentional contamination that could harm consumers and disrupt operations.

What is Food Defense?
With an understanding of the regulatory requirements, now we can dive into your food defense program, starting with the basics – What is food defense?
Food defense is the protection of the food supply from intentional contamination.
Unlike food safety, which focuses on preventing unintentional contamination from sources like pathogens or spoilage organisms, food defense emphasizes protecting against deliberate acts meant to harm consumers or disrupt supply chains.
History has shown that these threats are not just theoretical. For example, in 2018, Australia faced a significant food-tampering crisis when sewing needles were discovered embedded in strawberries across multiple states.
This malicious act led to widespread public fear, substantial financial losses for farmers, and a nationwide recall of the fruit. The incident underscores the critical importance of robust food defense measures to protect consumers and maintain trust in the food supply chain.
What Does an Effective Food Defense Program Accomplish?
A well-executed food defense program accomplishes several crucial goals:
- Safeguards the public by helping to prevent intentional contamination.
- Protects a company’s brand and consumer trust.
- Ensures compliance with regulatory requirements to avoid penalties.
- Reduces the risk of costly recalls and potential legal action.
How to Create a Food Defense Plan
As the regulations state, a written food defense plan is required, which means it’s not enough simply to engage in various activities that help prevent intentional economically motivated adulteration or food fraud – you need to clearly document your plan and maintain it in writing. Here’s how to get started.
Step 1: Conduct a Vulnerability Assessment
This step is crucial for identifying the most susceptible points within your supply chain and facility.
Vulnerability assessments can include a site audit from food safety experts who can help identify gaps where vulnerabilities to adulteration could occur. EAS Consulting Group, a Certified Group company, includes several former FDA personnel who can perform a site audit.
You can also use digital tools, like our Food Fraud Vulnerability Assessment tool, to help identify gaps in your supply chain and processes.

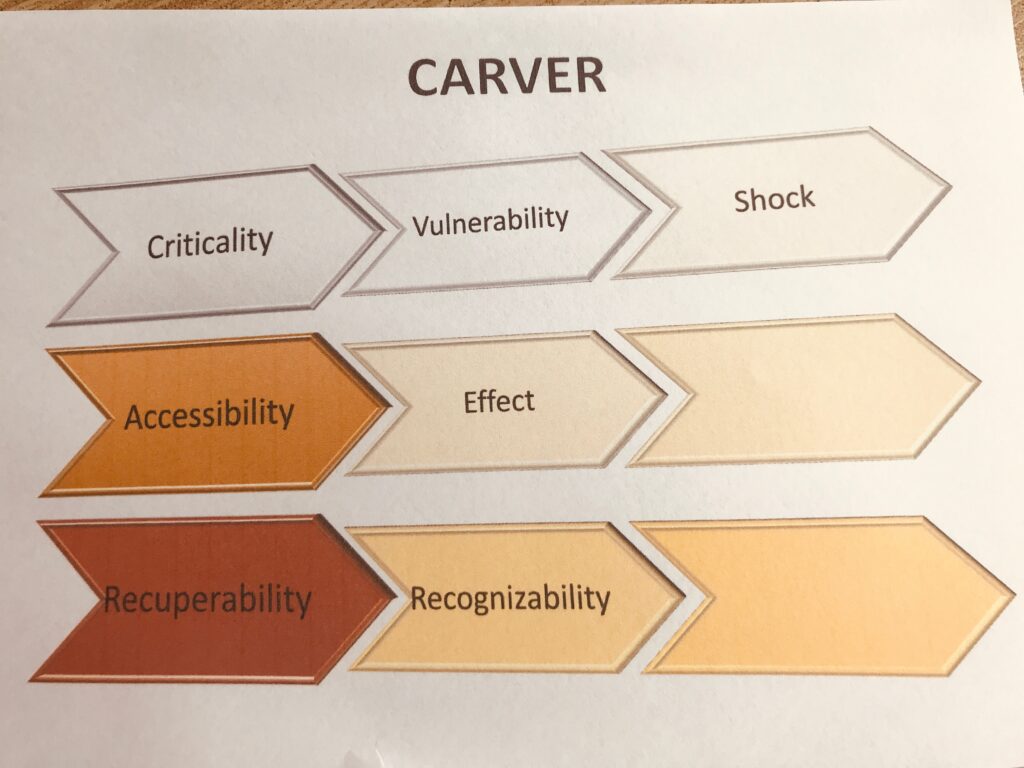
Additionally, risk evaluations using tools like CARVER + Shock are also a good idea. This method evaluates key factors, including…
- Criticality (the public health and economic impact)
- Accessibility (ease of physical access)
- Recuperability (ability to recover from an attack)
- Vulnerability (ease of executing an attack)
- Effect (loss resulting from an attack)
- Recognizability (ease of identifying the target)
The FDA offers its Food Defense Plan Builder, which is a digital tool that requires downloading and installing on your computer.

The gaps uncovered during the vulnerability assessment are as diverse as the products and facilities being assessed, but here are a few possibilities to help illustrate the point:
- Inadequate Access Control: Insufficient security measures at key entry points, allowing unauthorized individuals to access sensitive areas, such as production zones or ingredient storage.
- Limited Surveillance Coverage: Surveillance cameras or monitoring systems may not cover critical areas, such as loading docks, where materials enter or exit, creating blind spots for potential tampering.
- Poor Employee Screening and Training: A lack of thorough background checks for employees or contractors and insufficient training on recognizing and responding to suspicious behavior.
- Weak Recordkeeping Practices: Inadequate documentation of monitoring activities, corrective actions, and inspections can prevent a facility from meeting FDA documentation requirements and hinder audits.
- Vulnerable Packaging and Labeling: Packaging that is not tamper-evident or lacks secure labeling, increasing the risk of undetected contamination or adulteration in the final product.
Which tool or tools you use depends on the size and scope of your operation, in addition to the vulnerability of your products to adulteration. For some sites, an audit plus an evaluation using a digital assessment tool may be sufficient. For large, complex organizations, all the tools mentioned may be needed.
If you need help, the experts at EAS Consulting Group have designed food defense plans for several sites across multiple industries, so please contact them with questions.

Step 2: Develop Mitigation Strategies
Once vulnerabilities are identified, implement practical measures to prevent or reduce risks, such as…
- Secure access to sensitive areas by using biometric access controls or keycard systems to limit entry to authorized personnel.
- Use tamper-evident packaging to provide a clear indication of unauthorized access or tampering.
- Enhance surveillance by installing CCTV systems with remote monitoring capabilities to cover critical points such as entryways, production lines, and storage areas.
- Consider adding layered security measures like motion detectors and alarms for added protection.
Tailor these strategies to the specific needs of your facility, such as higher surveillance for high-value products or more stringent access control in areas handling allergenic or sensitive ingredients.
Step 3: Implement Monitoring Procedures
Once measures are implemented, ensure you monitor their effectiveness over time. This includes routine inspections, checks, and verification to confirm they are functioning as designed.
Use technology-driven tools like automated monitoring systems and digital dashboards to track data in real-time and promptly flag anomalies.
Incorporate periodic third-party audits for an unbiased review of your procedures and reinforce internal protocols through scheduled mock scenarios or drills.
These steps will help maintain a resilient and responsive food defense strategy.
Step 4: Train Your Team
A well-informed team is a critical part of any food defense plan. Regular training sessions should be conducted to teach staff how to recognize suspicious activities and respond appropriately. Ensuring employees are aware of their roles and responsibilities promotes a culture of vigilance.
FSNS offers several food safety training courses to help train your team. You can also monitor the EAS Consulting Group training and webinar schedules for training opportunities. Or, if you would like an in-house customized food defense course conducted for your team, EAS Consulting Group can assist.
Step 5: Maintain and Update the Plan
A food defense plan should be dynamic, evolving with new threats and regulatory changes. Writing a comprehensive food defense plan and maintaining it are crucial for ensuring that all procedures are well-documented and easily accessible for audits or inspections.
Consistent recordkeeping is essential, particularly to meet FDA requirements, which mandate thorough documentation to demonstrate compliance. Schedule regular reviews and updates to adapt to emerging risks, incorporate lessons learned, and ensure ongoing adherence to current regulations.
This continuous approach helps maintain the integrity and effectiveness of the plan over time.
Food Defense Plan Example
It helps to see an example of the contents of a food defense plan when writing your own plan. Here is an example using a common vulnerability identified using the Carver + Shock method mentioned above:
Vulnerability: Unauthorized access at the loading dock.
Description: The loading dock is a critical point for incoming raw materials and outgoing finished products. Due to its location and level of activity, it presents a risk for unauthorized access, which could lead to intentional adulteration or contamination of food products.
Assessment Details:
- Criticality: High – The loading dock is a main entry point for materials, posing a high risk to product safety if contaminated.
- Accessibility: Moderate – The area is accessible from outside the building but generally monitored by staff during active hours.
- Recuperability: Moderate – Recovery from a contamination event here could require extensive product recalls.
- Vulnerability: High – High volume of activity at the dock creates opportunities for unauthorized individuals to access the area undetected.
- Effect: Severe – A contamination event at this stage would affect a large volume of products.
- Recognizability: High – The loading dock is clearly marked, making it an identifiable target.
Mitigation Strategies
Access Control:
- Implement a keycard access system for dock entry to restrict access to authorized personnel only.
- Ensure dock doors are closed when not actively loading or unloading.
Surveillance:
- Install CCTV cameras covering the loading dock and entrances.
- Review camera footage daily and flag any unusual activity.
Employee Training and Awareness:
- Train staff on the importance of food defense and reporting suspicious behavior.
- Display “Authorized Personnel Only” signs prominently at the loading dock entrance.
Visitor Protocols:
- Require all visitors to sign in at the front office and receive an escort to the loading dock if access is needed.
Monitoring Procedures:
- Weekly Access Audit: Review access logs to verify that only authorized personnel accessed the loading dock.
- Daily CCTV Review: Designated personnel review surveillance footage each morning to ensure no unauthorized activity occurred overnight.
- Monthly Vulnerability Assessment Review: Re-assess the loading dock’s security measures and update protocols if needed.
Corrective Actions (if Vulnerability Detected):
- Immediately secure the loading dock area if unauthorized access is detected.
- Conduct a product inspection to ensure there has been no tampering or contamination.
- Notify food defense team lead and document the incident.
- Implement additional controls if a security gap is identified.
Verification and Validation:
- Internal Audit Frequency: Quarterly internal audits by the food defense team to validate the effectiveness of access control and surveillance measures.
- Training Review: Conduct refresher training on food defense for loading dock staff every six months.
Recordkeeping and Documentation:
- Access Logs: Retain records of keycard access for at least one year.
- CCTV Footage: Store footage for a minimum of 30 days or as required by company policy.
- Audit Reports: Document findings and corrective actions from quarterly audits and keep on file for FDA inspection readiness.
Need Help Creating a Food Defense Plan?
Developing and maintaining a comprehensive food defense plan is essential but complex. Assessing vulnerabilities, implementing strategies, and ensuring compliance can be challenging. Proper documentation and regular updates are key for meeting FDA requirements and preventing intentional contamination.
Partnering with experts like EAS Consulting Group can simplify this process, ensuring your plan is thorough, compliant, and adaptable to changing risks, ultimately protecting your business and consumers.
Contact EAS Consulting Group now to discuss your food defense system.



