Reviewed and Approved by Tim Lombardo, Senior Director, Food Consulting Services, EAS Consulting Group, a Certified Group company.
1-Minute Summary
- Conducting a Food Fraud Vulnerability Assessment is a requirement for GFSI-benchmarked food safety certifications and crucial for brand protection and public health.
- Regulatory requirements from the FDA and GFSI standards like SQF, BRCGS, and FSSC 22000 mandate specific procedures for identifying food fraud risks in your supply chain.
- The Vulnerability Assessment process systematically evaluates factors like ingredient sourcing, supply chain complexity, and supplier verification to identify weak points that are susceptible to food fraud.
- Use scoring systems to assess risk factors and conduct Severity Assessments to generate an overall Food Fraud Risk score.
Food Fraud Vulnerability Assessment: Safeguarding Public Health and Protecting Your Brand
Conducting a food fraud vulnerability assessment is a major component of your overall Food Fraud Program. It’s a requirement for GFSI-benchmarked food safety certifications. And it’s important for safeguarding public health and protecting your brand.
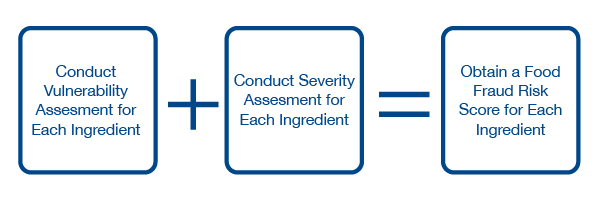
This article focuses on how to perform a food fraud vulnerability assessment, sometimes called a food defense vulnerability assessment. We’ll also show you how to perform a Severity Assessment to obtain an overall Food Fraud Risk score for each consideration in your supply chain.

What are the FDA Regulations Regarding Food Fraud?
Before diving into performing a vulnerability assessment, let’s cover the regulatory and industry requirements regarding your Food Fraud Program.
FDA: Food Safety Modernization Act (FSMA)
The FDA’s approach to food fraud prevention is rooted in the Food Safety Modernization Act (FSMA) of 2011, specifically the two rules listed below:
- Preventive Controls for Human Food (PCHF) and Animal Food (PCAF) Rules: Require food facilities to implement a written food safety plan that includes an analysis of hazards and risk-based preventive controls. While these regulations do not explicitly mention food fraud, they do require preventive controls to significantly minimize or prevent adulteration, which is a type of food fraud.
- Foreign Supplier Verification Program (FSVP) Rule: Requires importers to verify that their foreign suppliers are producing food in compliance with U.S. safety standards. Includes verifying that suppliers have controls in place to prevent intentional adulteration, which includes certain types of food fraud.
What are GFSI Requirements for Food Fraud?
SQF, BRCGS Food Safety, FSSC 22000, and others all include requirements for conducting a Vulnerability Assessment as part of your Food Defense Program. Here’s a rundown of the requirements:
SQF
Section 2.7 Food Defense and Food Fraud
- 2.7.1.4: “The food defense threat assessment and prevention plan shall be reviewed and tested at least annually or when the threat level, as defined in the threat assessment, changes. Records of reviews and tests of the food defense plan shall be maintained.”
BRCGS Food Safety
Section 5.4 Product Authenticity, Claims, and Chain of Custody
- 5.4.3: “A documented vulnerability assessment shall be carried out on all food raw materials or groups of raw materials to assess the potential risk of adulteration or substitution.”
FSSC 22000
Section 2.5.4 Food Fraud
- 2.5.4.1: “The organization shall have a documented and implemented vulnerability assessment procedure in place…”
What is a Food Fraud Vulnerability Assessment?
A Food Fraud Vulnerability Assessment is a critical tool that helps identify potential vulnerabilities in your supply chains that might make your business susceptible to food fraud.
It involves systematically evaluating each of your ingredients in isolation, its supply chain, and the control measures in place to determine where the gaps lie. The process requires you to ask the right questions to assess safety and quality, such as…
- Do my ingredients have a history of food fraud?
- Where are my ingredients sourced from?
- What degree of processing do my ingredients require?
- How complex is my supply chain?
- What controls do I have in place to ensure authenticity?
- How robust are my supplier verification processes?
If it sounds daunting, it doesn’t have to be if you follow some simple guidelines. Let’s walk through the process using our Food Fraud Vulnerability Assessment template.
Food Fraud Vulnerability Assessment Example
This checklist uses a scoring system that helps assess risk for several considerations throughout your manufacturing process.
Food Fraud Vulnerability Assessment Template
| Vulnerability | Score | |||
| Raw Materials & Packaging | History of Fraud | 1 | 3 | 5 |
| Economic & Geopolitical Considerations | 1 | 3 | 5 | |
| Supply Chain | 1 | 3 | 5 | |
| Supplier Relationship & History | 1 | 3 | 5 | |
| Raw Materials QC | 1 | 3 | 5 | |
| Processing & Distribution | Storage & Traceability | 1 | 3 | 5 |
| Calibration | 1 | 3 | 5 | |
| Hygiene & Cleaning | 1 | 3 | 5 | |
| Human Resources | 1 | 3 | 5 | |
| Information Given to Customers | 1 | 3 | 5 | |
| Subcontracting (if required; otherwise score 0) | 0/1 | 3 | 5 | |
To conduct your vulnerability assessment, begin with a single ingredient and assign a score for each consideration as follows:
- 1 = Low Vulnerability
- 3 = Medium Vulnerability
- 5 = High Vulnerability
Let’s use the example of turmeric. Begin by assigning it a Vulnerability Assessment score for “History of Fraud”. The information below will help you assign the appropriate score for each consideration.
Let’s say there have been a moderate number of reports of fraud, but no official alerts. You would assign a score of 3 for “History of Food Fraud”.
Next, assign a score for “Economic and Geopolitical Considerations”, and so on until you’ve completed the list.
History of Fraud
- Low Vulnerability: No reports or evidence of fraud in similar or equivalent ingredients.
- Medium Vulnerability: Moderate/high number of reports, but no official alerts from authorities.
- High Vulnerability: High number of reports. Alerts from authorities.
Economical and Geopolitical Considerations
- Low Vulnerability: One or more components with geographic origins that have little cause for concern.
- Medium Vulnerability: One or more components with geographic origins or that has been transported through regions of political concern. Anomalies detected frequently but are unrelated.
- High Vulnerability: One or more components with geographic origins or that has been transported through regions with increased concern. Anomalies detected that are related to each other.
Supply Chain
- Low Vulnerability: All production originates with the company. Suppliers act ethically and with quality policies.
- Medium Vulnerability: All raw materials originate from a single suppler, which may not manufacture its products, or which may purchase ingredients from a secondary supplier.
- High Vulnerability: Several ingredients, each manufactured by a different supplier.
Relationship with Supplier & History
- Low Vulnerability: Known and trusted supplier that always supplies the same ingredient. No known issues; past issues have been resolved. Supplier holds valid third-party certification. Obtains approval for any new ingredients.
- Medium Vulnerability: Established supplier with a short period of previous business or who is respected in the industry. Has had an issue that was not resolved appropriately.
- High Vulnerability: Non-established supplier. Ongoing issues that are not resolved appropriately. Evidence that appropriate checks not being made.
Raw Material Quality Control
- Low Vulnerability: Raw materials and packaging materials verified. Temperature monitoring conducted during transport. Weight controls applied. Processing aids comply with U.S. regulations.
- Medium Vulnerability: Raw materials, processing aids, and packaging approved, but no control testing performed. Transport conditions checked via checklist; weight of certain batches checked but without validated procedures or calibrated scales.
- High Vulnerability: Materials not verified. Temperature and weight checks not conducted. Processing aids lack appropriate certificate.
Storage & Traceability
- Low Vulnerability: Storage established and indicated for each material. Computerized management of traceability throughout production chain. Ingredients identified individually throughout processing. Full traceability of all finished product batches monitored.
- Medium Vulnerability: No area dedicated for each product but clear identification. Traceability performed manually.
- High Vulnerability: Location of materials not established in warehouse and products not identified individually. No traceability monitoring.
Calibration
- Low Vulnerability: Robust calibration plan. All instruments calibrated and periodically checked. Plan defines tolerances for all equipment.
- Medium Vulnerability: Calibration and verification plan established, but not all equipment is periodically calibrated.
- High Vulnerability: No calibration plan.
Hygiene & Cleaning
- Low Vulnerability: Sanitation plan for intermediate and final cleaning established that accounts for the product handled before and after cleaning. All detachable parts cleaned before each raw material change.
- Medium Vulnerability: Generic cleaning procedures that do not consider raw material changes.
- High Vulnerability: No generic cleaning procedures.
Human Resources
- Low Vulnerability: Operators have received extensive training about GMPs, traceability, and food fraud. Personnel responsible for internal product traceability receive specific training. Annual refresher training provided.
- Medium Vulnerability: Generic traceability and GMP training provided. Personnel not trained on specific food fraud issues; refresher training not provided.
- High Vulnerability: GMP training provided. No food fraud or traceability training provided.
Information Given to Customers
- Low Vulnerability: Regular checks made on correlation between raw materials origin/processes and specifications on the Technical Data Sheets and labels. Legality verified of all info provided on packaging material.
- Medium Vulnerability: Legality of information provided to customers checked regularly, but not verified.
- High Vulnerability: No check of information provided to customers.
Sub-Contracting
- Low Vulnerability: Service provider is known and trusted. Approval complies with standard procedures. Contractor has good food safety history and has regular third-party audits, preferably GFSI.
- Medium Vulnerability: Service provider is approved, but they define and control the type and conditions of processing. Contractor has good food safety history and has regular third-party audits, preferably GFSI.
- High Vulnerability: Service provider not approved and does not have food safety certifications. Third-party audits not conducted.

Conduct a Food Fraud Severity Assessment
Once you’ve completed the Vulnerability Assessment, it’s time to assign a Severity Assessment for each consideration using the scores you have just generated. We’ll review an example soon, but let’s first explain the Severity Assessment.
For each ingredient in your finished product, apply a Severity Assessment to gauge overall risk of food fraud. This entails aligning each consideration during the Vulnerability Assessment with one of the category descriptions below:
| Severity Assessment | |
| Low Severity (1) | Adulterant corresponds to a negligible percentage of total product. Product complies with all applicable standards and does not affect public opinion. |
| Medium Severity (3) | Accumulation of adulterant may cause non-fatal injuries or harm to long-term health. Adulterant corresponds to a non-negligible percentage of total product. Adulterated product does not comply with current standards and operator may be committing a serious breach. |
| High Severity (5) | Fraudulent product contains an allergen or may cause illnesses with serious or potentially fatal consequences. If adulterant considerably reduces nutritional content, it could cause a public health problem. Adulterated product does not comply with current food safety standards and operator may be committing a serious crime. Product has media pressure and its adulteration generates major controversy among public opinion. |
Food Fraud Severity Assessment Example
Let’s review using our turmeric example. In our Vulnerability Assessment, we assigned a score of 3 for “History of Food Fraud”.
In our Severity Assessment, we realize that the adulterant in our turmeric corresponds to a non-negligible percentage of the total product. Plus, it could lead to long-term health consequences. For these reasons, we assign it a score of 3 in our Severity Assessment, indicating Medium Severity.
Putting it all Together: Food Fraud Risk
Let’s put it all together to generate a score that indicates our Food Fraud Risk in our assessment of turmeric for this consideration.
Vulnerability Assessment (3) + Severity Assessment (3) = 6 (Medium Risk of Food Fraud)
This means that we have a medium risk of food fraud for this consideration. Now, complete the same process for each consideration to gauge your food fraud risk. Areas of high risk (8-10) should trigger your mitigation plan.
By conducting a detailed and well-thought-out Vulnerability and Severity Assessment for each ingredient, you can pinpoint where your greatest risks lie. These assessments provide an understanding of potential food fraud threats.
Armed with this knowledge, you can strategically plan and implement effective mitigation tactics to protect your supply chain, uphold food safety standards, and safeguard consumer trust in your products.
Use our complimentary Food Fraud Vulnerability Assessment tool to begin assessing your risk now.



